Technologies
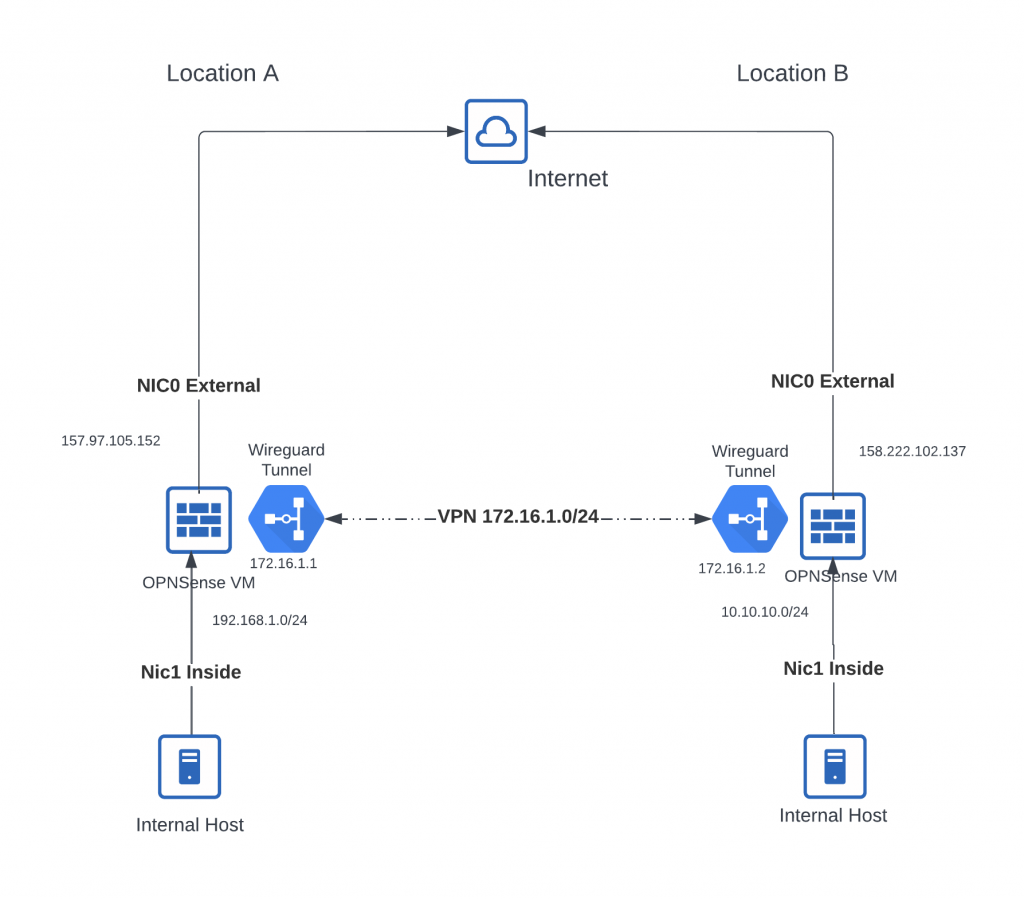
VPN tunnels are used to connect on-prem and virtual locations across the internet in a secure tunnel. Using the Open Source firewall project of OPNSense along with the Open Source Wireguard VPN we will connect two locations.
Step 1: Build an OPNSense instance
Time: ~20 minutes
- Download the OPNSense ISO from https://opnsense.org/download/ be sure to select DVD in the second drop down and then click Download
- Upload the OPNSense ISO to the datacenter location video instructions here https://ionoslabs.com/index.php/ftp-iso-upload/
- Create the Virtual Data Center in the desired geographical location
- Create your OPNSense instance by dragging and dropping the server icon to the DCD grid
- Use an IONOS Cube instance if available with 1 or 2 vCPU’s
- Add a CD ROM and set it as Boot device, select the OPNSense image that you uploaded via FTP
- Install OPNSense with defaults
Step 2: Configure interfaces and add bastion host
In this step we will create a Windows bastion host. This host will have both an “Internal” interface behind the OPNSense firewall, and an “External” interface with a real IPv4 address. This is done so that we can configure the OPNSense firewall and tunnel without worrying that if we make a mistake that we will lock ourselves out.
Time: ~15 minutes
- Drag and drop a server instance to the DCD grid, connect the first interface to the “Internet Access” and the second interface to the OPNSense firewall by clicking the plus sign and dragging on the bastion host instance.
- Provision the changes to start the provisioning of the bastion server
Configure the Firewall Interfaces
- Reserve a static IP address to be assigned to the Firewall
- Assign the static IP address to the wan nic (nic0)
- Uncheck the assign DHCP Gateway for firewall WAN interface, Internal interface and bastion internal interface
- Provision the changes
- Open Console to Firewall instance (right click on instance)
- Assign interfaces to WAN and LAN and configure IP addresses
- Note: WAN static IP address will always be /24 (255.255.255.0) IP’s
- Note: Upstream gateway address will always be the same first 3 octets as the statically assigned IP, but last octet will be .1
- Test external connectivity by pinging an external address like 1.1.1.1
Remote Desktop into bastion host
- Find the assigned external IP address by selecting the bastion instance and then clicking on network to the right
- Open remote desktop client and enter IP bastion IP address to connect
- Login with username administrator and password that you previously set
Connect to internal OPNsense with a browser and username root and password previously set
Step 3: Build Internal host and verify internet connectivity
Build an internal host to verify connectivity through firewall
Time: ~5 minutes
- Drag and drop a Cube instance (if available) and connect only to internal LAN (LAN2)
Step 4: Build out B side of VPN
Build out B side for VPN
Time: ~20 minutes
- Drag and drop a Cube instance (if available) and add CDROM for FW B instance, begin OPNsense build
- Note: If building in another DC Region you will need to upload the OPNsense ISO to that region
- Drag and drop a Cube instance (if available) for Windows bastion host
- Connect both instances to Internet Access, create LAN 2 by connecting Bastion host to Firewall instance
- Drag and drop a Cube instance (if available) for Windows internal host, connect only to LAN 2
- Provision Changes
Configure FW B interfaces and Bastion Static IP
- Note: Add static address like A side
- Note: Internal address range cannot be the same as A side
- Provision Changes
- Reboot internal host to get new DHCP address as needed
- Verify external connectivity from firewall by performing ping to 8.8.8.8
Step 4: Install WireGuard and build VPN tunnel
Install WireGuard and build VPN tunnel
Time: ~20 minutes
Login to Location A
- Open Remote Desktop Session to bastion host A
- Login to OPNsense Firewall A via web GUI and update Firewall A
- After update and restart, install the WireGuard plugin
Enable WireGuard and create Local config FW A
- Go to VPN –> WireGuard and enable WireGuard
- Create new Local Config
- Leave blank Public and Private Keys, these will be generated automatically
- Set listen port to 51820
- Set Tunnel address to 172.16.1.1/24
- Save and Apply
Login to Location B
- Open Remote Desktop Session to bastion host B
- Login to OPNsense Firewall A via web GUI and update Firewall B
- After update and restart, install the WireGuard plugin
Enable WireGuard and create Local config FW B
- Go to VPN –> WireGuard and enable WireGuard
- Create new Local Config
- Leave blank Public and Private Keys, these will be generated automatically
- Set listen port to 51820
- Set Tunnel address to 172.16.1.2/24
- Save and Apply
- Open Local config and copy Public Key
Return to Location A
- Go to VPN –> WireGuard –> Endpoints and add new endpoint
- Enter name for endpoint as FWB
- Paste Public Key from FWB into Public Key section
- For Allowed IP’s Enter the Tunnel address from FWB 172.16.1.2/32 and Internal IP Range from FWB 10.10.10.0/24
- For Endpoint Address Enter the IP address of the WAN interface of FWB (the reserved static IP address)
- For Endpoint Port enter 51820 and then Save and Apply
- Now copy the public Key from FWA
Return to Location B
- Go to VPN –> WireGuard –> Endpoints and add new endpoint
- Enter name for endpoint as FWA
- Paste Public Key from FWA into Public Key section
- For Allowed IP’s Enter the Tunnel address from FWA 172.16.1.1/32 and Internal IP Range from FWB 192.168.1.0/24
- For Endpoint Address Enter the IP address of the WAN interface of FWA (the reserved static IP address)
- For Endpoint Port enter 51820 and then Save and Apply
- Go to VPN –> WireGuard –> Local Config
- Go to the Peers drop down and select FWA
- Save and Apply
- Add Firewall Rules FWB
- Go to Firewall –> Rules –> WAN
- Add rule to Allow port 51820 to WAN Address
- Save and Apply
- Go to Firewall –> Rules –> WireGuard to allow traffic from Location A
- No changes to rule required, leave defaults and Save and Apply
Return to Location A
- Add Firewall Rules FWA
- Go to Firewall –> Rules –> WAN
- Add rule to Allow port 51820 to WAN Address
- Save and Apply
- Go to Firewall –> Rules –> WireGuard to allow traffic from Location B
- No changes to rule required, leave defaults and Save and Apply
- Go to VPN –> WireGuard –> Local Config
- Go to the Peers drop down and select FWB
- Save and Apply
Test Connectivity
- From Internal Host A or Bastion Host A ping 10.10.10.100 (bastion host B)
- Test Remote Desktop Connection to Bastion host B on internal IP address 10.10.10.100 from Bastion Host A
